Blog
ByteJams Files Patent Application:
Unified Method and System for Detecting Ransomware and Data Exfiltration
At ByteJams, we're excited to announce that we have officially filed a patent application for:
"Method and system for detecting ransomware and/or data exfiltration"
This milestone reflects decades of cybersecurity expertise and addresses the growing complexity of today's threats.
Modern ransomware attacks have become highly sophisticated, frequently combining encryption with data theft — a tactic known as double extortion. Despite significant advancements in threat detection technologies and artificial intelligence, ransomware continues to pose a critical threat to organizations worldwide.
Our patent application outlines an innovative, unified algorithm designed to detect both ransomware and data exfiltration activities by identifying adversary techniques, rather than relying on traditional signatures or predefined patterns. This autonomous, endpoint-based approach ensures resilient protection against novel, unknown, or rapidly evolving threats — without dependence on cloud services, external threat intelligence feeds, or frequent signature updates.
This technology serves as the foundation for ByteJams Ranger, our lightweight, continuous protection solution that defends against encryption-based attacks and data exfiltration — with minimal operational overhead and no manual configuration requirements. With Ranger, organizations can protect their documents and files, even against emerging and unknown threats.
While the algorithm marks a breakthrough, Ranger's architecture sets a new standard for endpoint protection design. We’ll dive deeper into this innovation in an upcoming post.
At ByteJams, we believe cybersecurity must be autonomous, efficient, and deeply embedded where it matters most: at the endpoint. Filing this patent application marks a significant milestone in our mission to redefine endpoint security for today’s rapidly evolving threat landscape.
We extend our thanks to Custos IPC for their valuable support throughout the patent application process. Custos IPC
Ransomware's Evolution: Remote Encryption Is Now the Primary Weapon
Over the past decade, ransomware has evolved from simple local attacks into complex operations where remote encryption has become the primary weapon of choice. From the early days of CryptoLocker in 2013 to modern threats like RansomHub, ransomware families have consistently refined their techniques to encrypt files faster, spread wider, and bypass detection more effectively.
According to the Microsoft Defense Report 2024, over 90% of ransomware attacks now originate from unmanaged or compromised devices. Microsoft
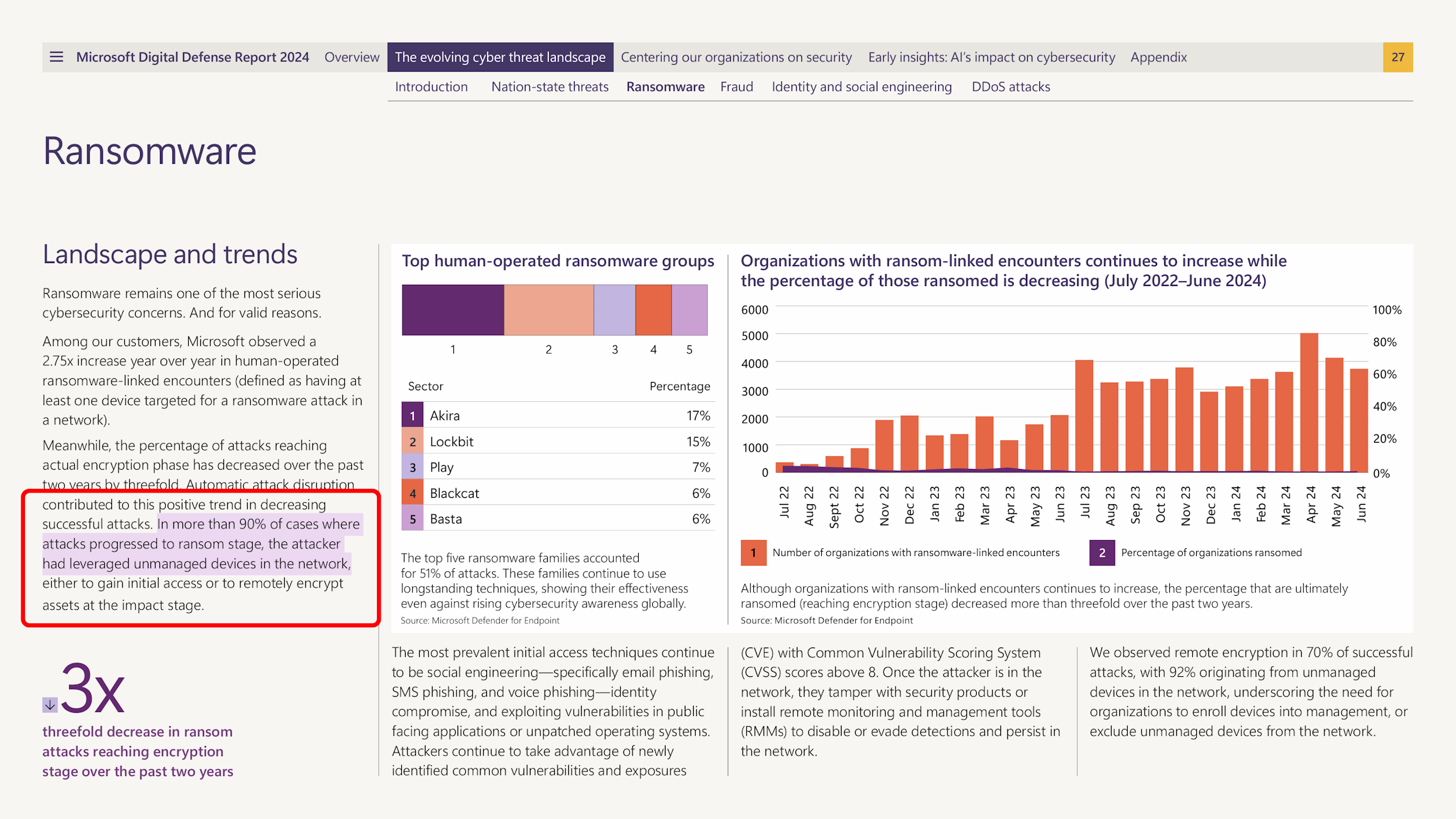
Source: Microsoft Digital Defense Report 2024 (Page 27)
These figures show how ransomware attacks have shifted toward using compromised or unmanaged endpoints to encrypt shared resources, bypassing traditional endpoint protection. Understanding the shift toward so-called remote ransomware is critical to building real-world defenses.
So what is remote ransomware?
Local ransomware runs on the same machine where the targeted files reside, encrypting data directly. Remote ransomware, on the other hand, attacks files stored on a different system — typically over a network share or mapped drive.
This difference matters because with remote ransomware, the malicious process is happening elsewhere. The file server only sees normal file operations: files being opened, modified, and saved. It never sees the encryption program or any suspicious behavior locally. As a result, endpoint protections based on local file scanning, memory analysis, or process monitoring are ineffective. These techniques can only detect threats that execute on the endpoint itself, not those operating across the network.
Since CryptoLocker in 2013, ransomware has had one goal: encrypt files fast. Attackers use multi-threading, partial encryption, and memory-mapped access to speed things up. From the start, ransomware has targeted both local and network-mapped drives, as applications treat such drives the same way.
Real-world examples show how ransomware families deliberately exploit this behavior. Many variants specifically target remote file shares, sometimes encrypting only parts of each file to reduce network traffic. Encrypting faster means hitting more systems before detection.
Once attackers compromise a device, they rarely stop after a blocked attempt. If direct ransomware deployment is prevented by local defenses, they often pivot, using the compromised device to remotely encrypt data across the network. In these attacks, the only visible activity is legitimate-looking file traffic — plain documents are sent out and encrypted files are returned — making detection extremely difficult, as the malicious process performing the encryption runs on the compromised endpoint.
The Akira ransomware group recently demonstrated this technique by pivoting to an unsecured Linux-based webcam after their initial Windows-based encryptors were blocked. Using the webcam, they mounted SMB shares and remotely encrypted critical files without triggering endpoint detection. Since the device was unmanaged and lacked any monitoring, the malicious encryption traffic went unnoticed until after the damage was done. Bleeping Computer
Remote ransomware is not limited to niche threat actors. Well-known ransomware families including Akira, BlackCat, Conti, LockBit and RansomHub include remote encryption as part of their standard toolkits. A single unmanaged or under-protected device is enough to put the entire organization at risk, regardless of how well other systems are secured.
Protection against remote ransomware
While endpoint security products have evolved, much of the industry's investment has gone into managed detection and response (MDR) solutions that focus on detecting early attack signals — such as privilege escalation, lateral movement, or command-and-control activity. However, far less attention has been given to stopping the actual act of file encryption itself. In remote ransomware scenarios, where the malicious encryption happens off-device, this gap leaves critical blind spots that traditional endpoint defenses and MDR services often miss.
As ransomware operators continue refining their methods, remote ransomware has become the norm. Defense strategies must adapt. Relying solely on endpoint detection, traditional anti-virus, or Managed Detection and Response (MDR) solutions is not sufficient when the attack doesn't even run on the server itself.
ByteJams Ranger addresses this challenge head-on. It detects both local and remote ransomware encryption in real time, isolates the compromised endpoint to stop the adversary from continuing the attack, and automatically rolls back any affected files to their original state. By working autonomously on the device, without relying on external threat intelligence or cloud analysis, Ranger provides true universal file protection — securing both local and remote data against modern encryption attacks, regardless of file size or type.


