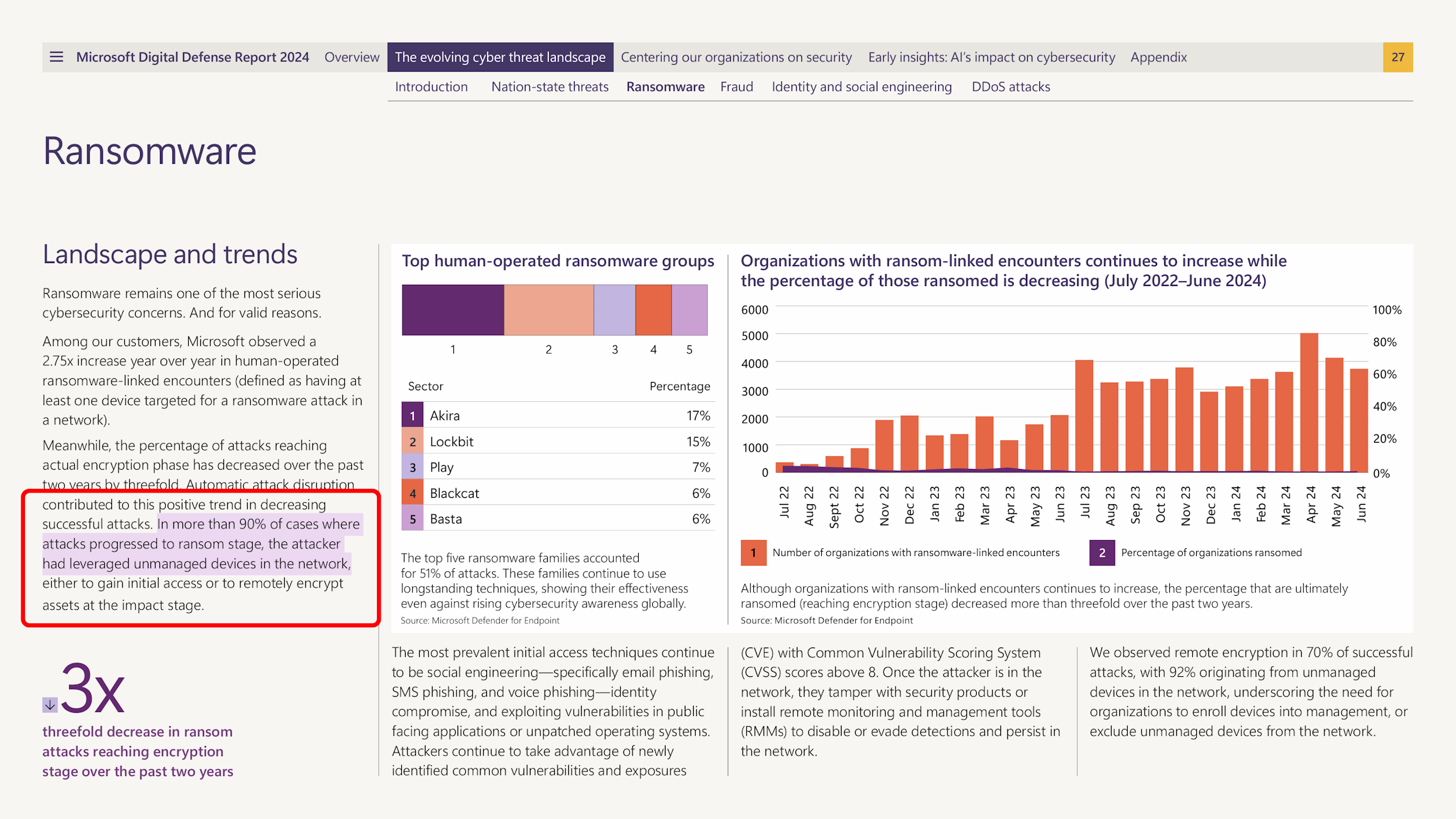
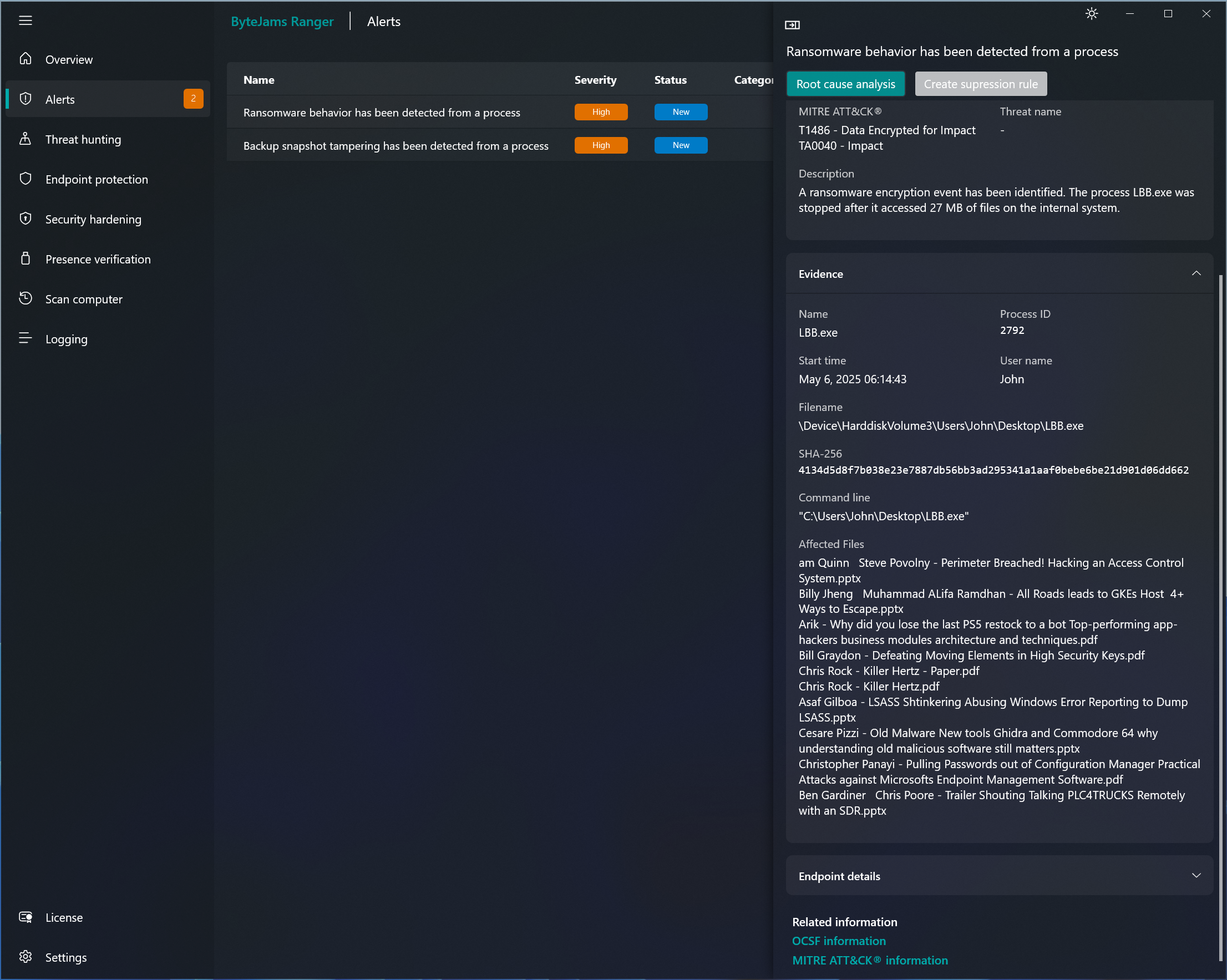
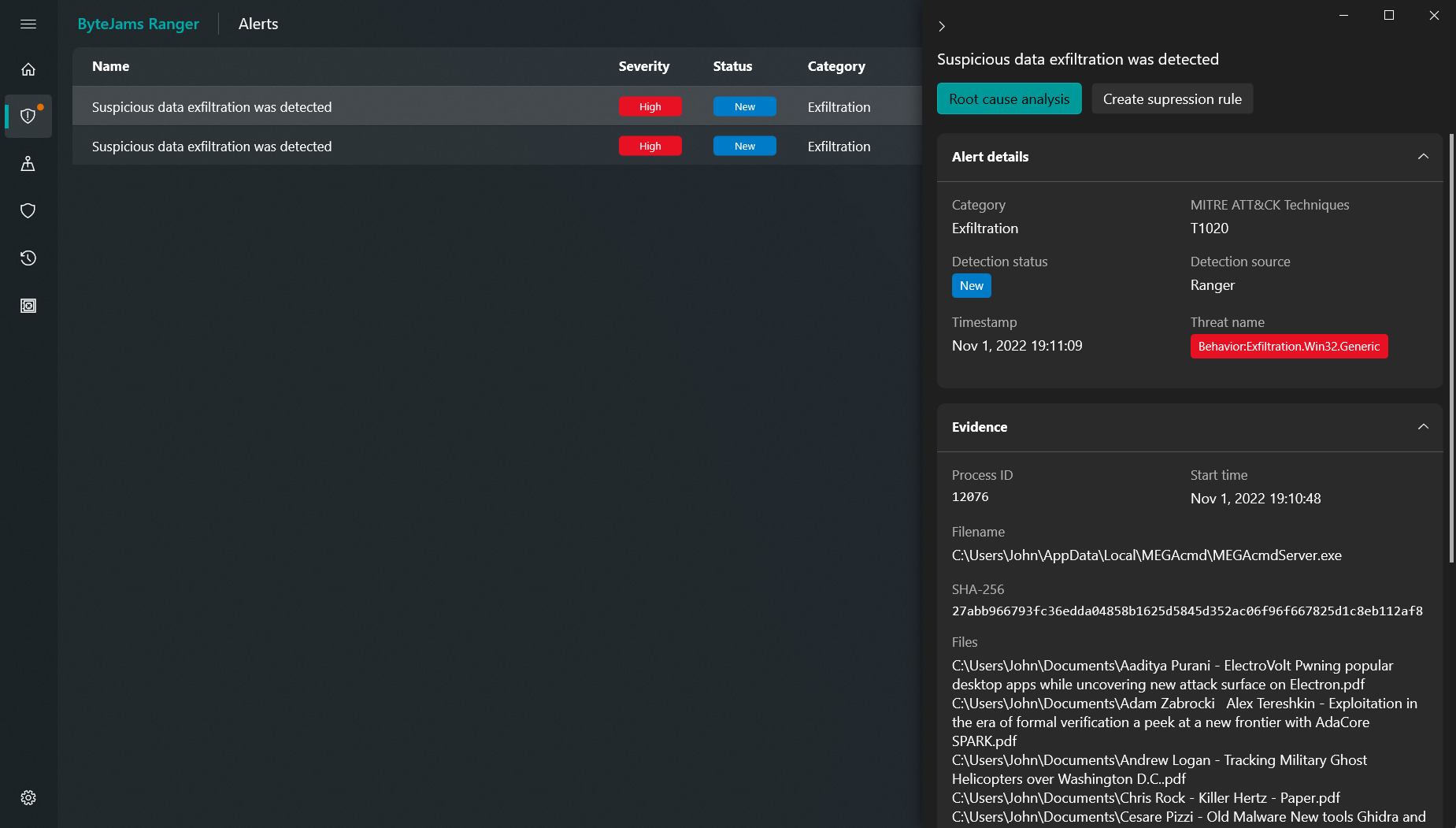
Company
ByteJams B.V. is a Dutch cybersecurity startup founded by an industry veteran with over 20 years of experience,
whose technologies successfully protect more than 50 million devices worldwide.
ByteJams introduces a patent‑pending, kernel‑free architecture that safeguards system stability and
preserves peak application performance, while delivering next‑generation protection against human‑led cyberattacks.
Unlike traditional solutions — including AI‑based defenses — ByteJams not only detects threats but disrupts
the fundamental techniques attackers rely on.
Leveraging deep expertise in Windows internals and data flow, ByteJams enables real‑time interception of ransomware
encryption and data exfiltration, even from previously unknown threats — setting a new standard for future‑proof cybersecurity.